Data Security & Protection
Protect Your Data First,
Not Last
On average, 20% of an organization’s data is accessible to every employee. Seventy percent of data breaches take months or years to discover.
But not for our customers. DBTRONIX helps you find risk, reduce risk, and keep it from coming back.
Put data protection on autopilot
It only takes one compromised endpoint to cause a headline-making data breach if your data is overexposed and unmonitored. Every CISO wants to prove to the board that they are actively reducing risk. With Automation Engine, you can safely automate risk reduction in days, not years.
“It’s not a priority right now.”
THE SIX MOST REGRETTED WORDS IN IT
Why is data so vulnerable? Finding your biggest data security risks is harder than ever. Prioritizing risk, safely fixing issues, and keeping data protected requires visibility and context that most organizations simply don’t have. Last year, we assessed a sample of 6.2 billion files, 459.2 million folders, and 5.5 petabytes of data for 130 companies across 30+ industries.
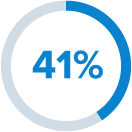
had over 1,000 sensitive files open to every employee
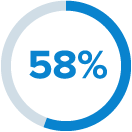
had 100,000+ folders open to everyone
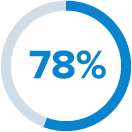
had over 1,000 stale sensitive files
Assess, prioritize, and mitigate your biggest IT security risks
Our dashboards show where you’re at risk, and track your progress as you lock things down. Quickly pinpoint exposed sensitive GDPR files on your NAS, stale data in Office 365, or risky Active Directory misconfigurations that hackers love to exploit.
Classify sensitive data
on-premises and in the cloud
Focus your data protection efforts on your most important data. DBTRONIX quickly and accurately classifies sensitive, regulated information stored in file shares, NAS devices, SharePoint, and Office 365. Apply labels to your files to enable DRM, encryption, and more.
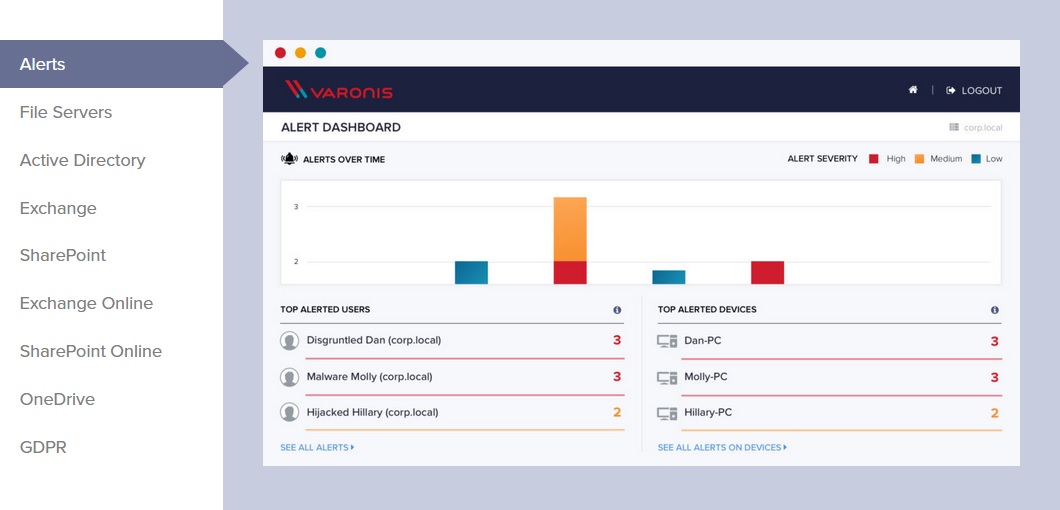
Search a Unified Audit Trail of Events
Know exactly what’s happening with your data and stop breaches before they happen.
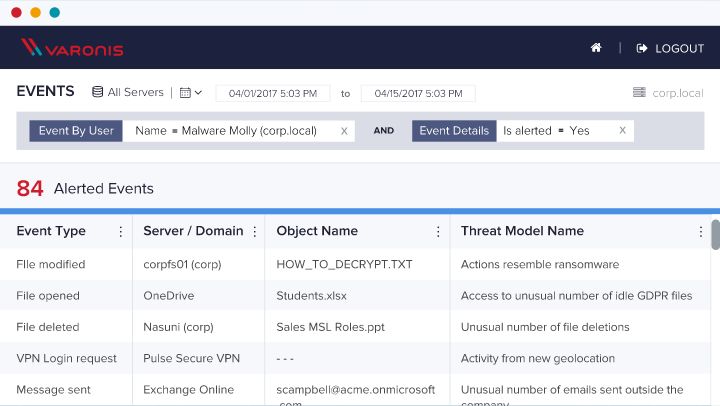
With a unified audit trail, admins or security analysts are only a few clicks away from knowing who’s been opening, creating, deleting, or modifying important files, sites, Azure Active Directory objects, emails, and more.
AI-Powered
Recommendations
Our machine learning algorithm flags users with unnecessary access. Acting on these recommendations is a fast and accurate way to reduce risk and get to least privilege. Model permissions changes in a sandbox and commit changes with just a few clicks.

Schedule a personalized
data risk assessment
Our free risk assessments are so actionable, consultants try to charge for them.
It’s true: our assessments pinpoint your vulnerabilities so accurately, others have tried to white label and sell them. That’s because they give you concrete steps to prioritize and fix major security risks and compliance issues in your data, like:
- Global access, stale data, and inconsistent permissions
- Overexposed sensitive data like PII, HIPAA, and PCI
- Non-compliant access and authorization processes

Resolve security incidents quickly and conclusively
DBTRONIX drastically reduces the time to detect and respond to cyberattacks – spotting threats that traditional products miss. By combining visibility and context from both cloud and on-prem infrastructure, DBTRONIX customers get:
- 90% reduction in response times
- Out-of-the-box threat models for the entire kill chain
- The #1 rated UEBA solution on Gartner Peer Insights
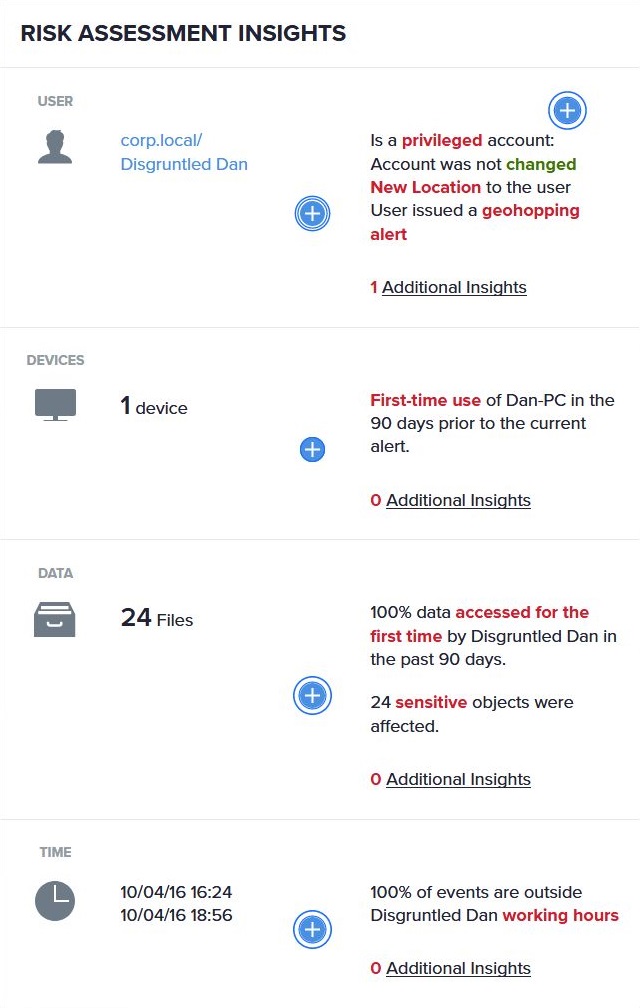
Proactively sustain a secure environment
Reducing risk is a big challenge, keeping risk under control requires automation
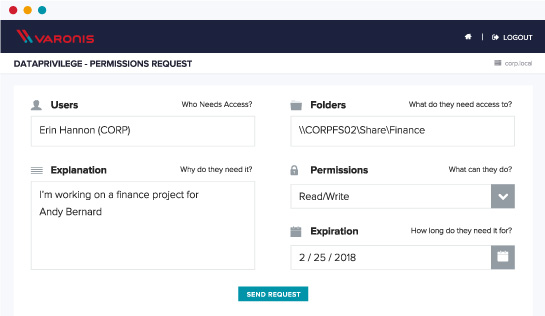
Automate authorization workflows
Authorization workflows let users request access to folders, groups, distribution lists, and SharePoint sites, folders, and lists through an easy-to-use web form. Each request is routed to the proper stakeholders based on the workflows you setup. Handling access requests is as simple as replying to an email. Once approved, access is automatically granted by DBTRONIX without any involvement from IT.
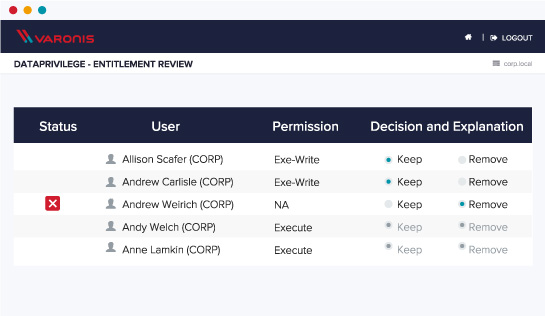
Automate entitlement reviews
Make sure that access to groups, distribution lists and sensitive business data is consistently reviewed by the right people. Certifications are delivered directly to data owners which lets them see who currently has access to their data and make changes without any involvement from IT. Our machine learning algorithms flag users that probably shouldn’t have access anymore, making reviews quick and easy.
Automate deletion
Enforce retention policies with ease using custom rules to move, archive, or delete data based on content type, age, access activity, and more. Quarantine sensitive and regulated content whenever it shows up in an unapproved locations.
Contact Us
We are here to help. Call us and speak with a secure erase specialist who will answer any questions you might have




