Privacy & Complance
Protect your regulated data and ensure compliance with DBTRONIX
Compliance starts with visibility, regardless of the standard
DBTRONIX gives you the enterprise-wide visibility you need for effective discovery, auditing, and compliance reporting across a wide variety of regulatory standards.
Perform on-demand risk assessments
Live risk dashboards and on-demand compliance reports give auditors and compliance teams real-time awareness of exposure, usage, ownership, and staleness.
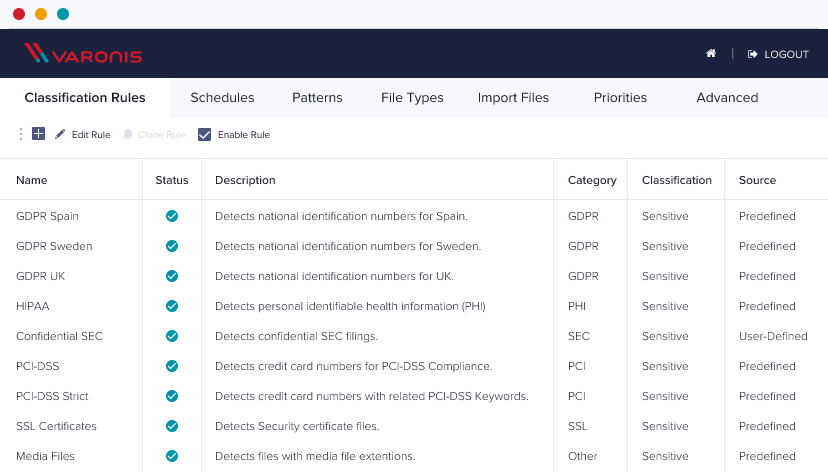
Discover regulated data with out-of-the-box policies
Every regulation requires unique patterns, validation algorithms, and exclusions. Our experts build, test, and deploy policies for every regulation so you don’t have to.
Prove the effectiveness of your security controls
Deliver hard evidence that demonstrates that you know where regulated data is, only the right people have access, and it is being processed according to policy.
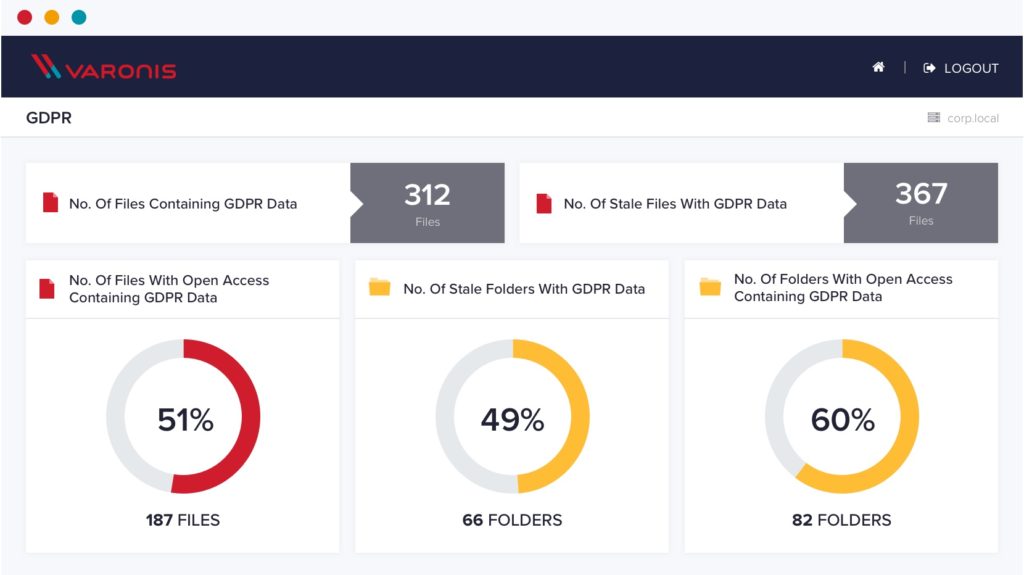
Classify regulated data with speed & accuracy
DBTRONIX quickly and accurately classifies sensitive, regulated information stored in on-premises and cloud data stores. Our classification engine prioritizes scans based on risk & exposure to give you actionable results quickly, no matter how much data you have.
Pinpoint Accuracy
DBTRONIX limits false positives and false negatives with flexible condition matching, algorithmic verification, proximity matching, smart filtering, and more.
Effortless Policy Updates
Get live updates to your classification library. New patterns and rules are shipped on a regular basis—no need to perform manual upgrades.
Customizable Classification
Build your own classification rules and dictionaries to meet organization-specific requirements. Add flags, tags, and notes to files and folders for reporting and policy enforcement.
400+ classification patterns to cover all your compliance needs

“DBTRONIX is extremely useful in meeting [compliance] demands, both for ourselves and our customers. Having a solution that can be configured to exacting specifications provides a powerful advantage for financial firms that face a high level of regulatory scrutiny.”
John Gracey , VP of Cybersecurity
Remediate risk & close your biggest compliance gaps
Visibility is just the beginning. DBTRONIX helps you find risk, reduce risk, and keep it from coming back so you can continually comply with data protection regulations.
Remediate overexposed data.
Eliminate unnecessary access to sensitive data safely and automatically to ensure data by design and by default.
Automate authorization workflows.
Ensure that each request to access regulated data is signed off by an approved data owner.
Automate entitlement reviews.
Show auditors that you have a process in place to regularly review access and revoke unnecessary permissions.
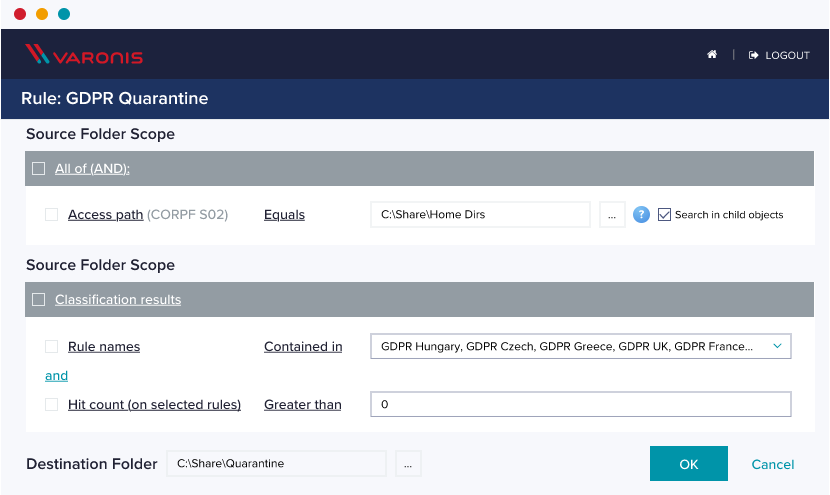
Enforce retention policies.
Create custom rules to move, archive, or delete data based on content type, age, access activity, and more.
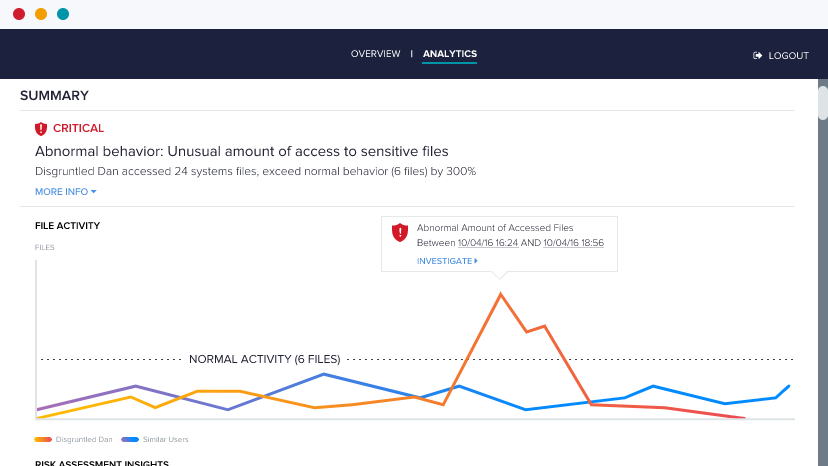
Detect unusual behavior on regulated data.
Quickly investigate and respond to potential cyberattacks and policy violations with a full forensic audit trail of data access.
Get persistent protection with labels.
Apply labels to files according to your policies to enable search, migration, remediation, encryption, rights management, and more.
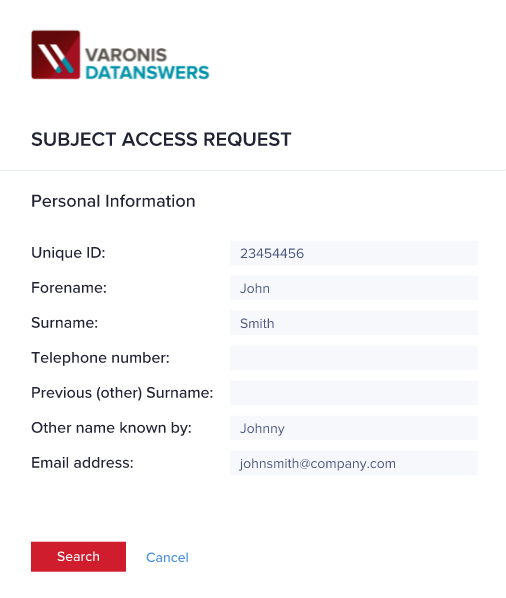
Quickly handle Subject Access Requests (SARs)
DBTRONIX helps you quickly find the regulated data you need and take action to flag, protect, archive, or delete it.
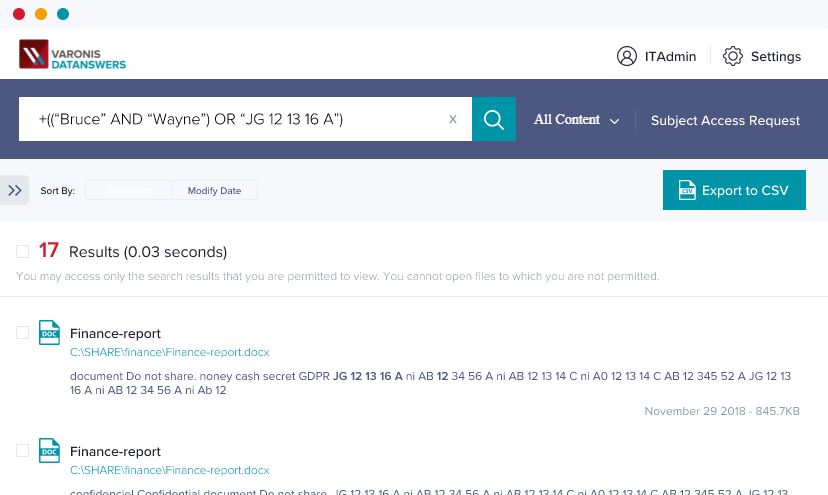
Find personal data quickly.
Easily export results.
Select and export search results in order to migrate, quarantine, or delete them.
Automate deletion.
Enforce retention policies with ease using custom rules to move, archive, or delete data based on content type, age, access activity, and more.
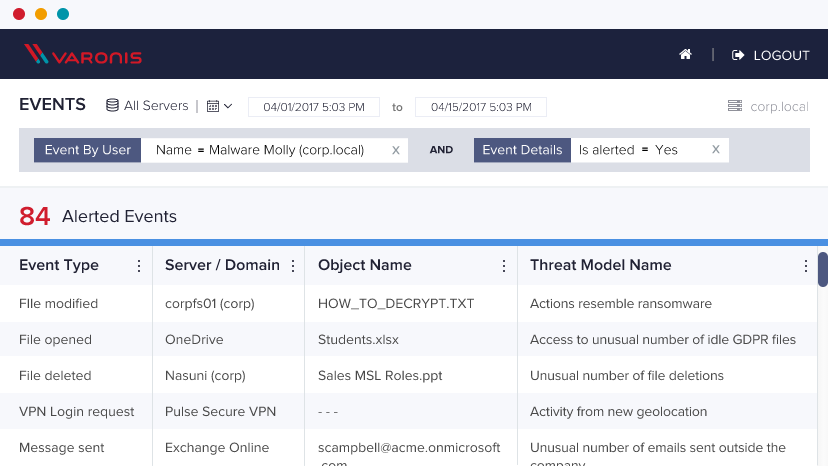
Detect threats to your regulated data
Get alerted when regulated data is under attack and comply with data breach notification timelines. DBTRONIX uses behavior-based threat models that give you meaningful alerts and a searchable audit trail so you know exactly what’s happening to your regulated data.
Access to an unusual number of idle GDPR files
Permission changes: Global Access Groups added to folder with significant GDPR data.
GDPR was data accessed in the past 24 hours
Low and slow increase in number of idle GDPR files accessed
Unusual number of GDPR files with denied access
An unusual amount of data was uploaded to an external website after accessing GDPR data
Unusual number of GDPR files deleted or modified
Abnormal service behavior: access to atypical folders containing GDPR data
An unusual amount of data was uploaded to email websites after accessing GDPR data
Contact Us
We are here to help. Call us and speak with a secure erase specialist who will answer any questions you might have